4.14. OTP KEYWRITER¶
Table of Contents
4.14.1. Introduction¶
Note
This document is applicable to High Secure (HS) device variants.
OTP (One Time Programmable) Keywriter is the software tool, used to provision customer keys into the device eFuses for enforcing secure boot and establishing root of trust. Secure boot requires an image to be encrypted (optional) and signed using customer keys, which will be verified by the SoC using the active MEK (for decryption) and MPK Hash (to verify the signature). In case the customer’s MPK and MEK are compromised, there is a second set of backup MPK and MEK fields that can be used, after applying a keyrevision update.
In order to burn the 2 sets (active and backup) of customer key information into the SoC, OTP Keywriter requires a x509 format certificate, signed using customer key(s) (Programming of backup key set is optional).
Note
This action is irreversible, so there is no going back once the keys are burned into SoC eFuses.
| Key | Description | Notes |
|---|---|---|
| SMPKH | Secondary Manufacturer Public Key Hash | SMPK is 4096-bit customer RSA signing key |
| SMEK | Secondary Manufacturer Encryption Key | 256-bit Customer encryption key for encrypted boot |
| BMPKH | Backup Manufacturer Public Key Hash | BMPK is 4096-bit customer RSA signing key |
| BMEK | Backup Manufacturer Encryption Key | 256-bit Customer encryption key for encrypted boot |
| KEYCNT | Key count | 2 if both BMPK & SMPK are used, 1 if only SMPK is used |
| KEYREV | Key revision | Active key revesion, 1 for SMPK, 2 for BMPK (can only be incremented - so keywriter should set to 1) |
| MSV | Model specific value | 20 bit value with 12 bit BCH code |
| MEK Options | SMEK/BMEK options | (Reserved for future use) 5 bit value |
| MPK Options | SMPK/BMPK options | (Reserved for future use) 10 bit value (split into 2 parts) |
| SWREV-BOARDCONFIG | Secure Board Configuration software revision | 128 bit value (64 without double redundancy) DO NOT PROGRAM - initial values set by TI |
| SWREV-SBL | SBL software revision | 96 bit value (48 without double redundancy) DO NOT PROGRAM - initial values set by TI |
| SWREV-SYSFW | Firmware software revision | 96 bit value (48 without double redundancy) DO NOT PROGRAM - initial values set by TI |
| EXTENDED OTP | (Reserved for future use) Extended OTP array | 1024 bit extended otp array |
Limitations
The current version of OTP Keywriter only supports 4096 bit RSA format for SMPK and BMPK. Support for ECDSA and different key lengths will be available in subsequent versions.
4.14.2. Components¶
OTP Keywriter contents include:
PDK keywriter app source code
This is the public keywriter application. It boots directly on the primary boot core of the device (generically, not necessarily R5) without any other bootloader. It is responsible for sending the OTP configuration to the secure keywriter component running on the security subsystem to blow the keys into the device eFuses.
- x509 certificate configuration template, and generation script as a part of source code
Note
This is a reference script. It can either be used as-is with the customer’s keys or integrated within the customer’s HSM environment.
Encrypted TIFS keywriter binary
This is the secure OTP keywriter firmware, and runs on the secure subsystem of the device (not necessarily M3, or even DMSC). It is responsible for verifying the OTP configuration from x509 certificate and blowing the data into the device efuses.
Note
This binary differs from the standard TIFS binary used in production.
TI FEK (public) key - TI Field Encryption Key
This will be required by the certificate generation script, to ensure confidentiality of the customer’s key material. TI FEK Public key will be used to encrypt content (refer Fig. 4.8), and TI FEK private key (not shared, but accessible by encrypted TIFS keywriter binary) will be used to decrypt it (inside the secure subsystem).
4.14.3. Directory Structure¶
keywriter/
|-- binary
| |-- j7200
| `-- j721e
|-- boardcfgs
| |-- j7200
| | |-- keywr_defaultBoardcfg_hex.h
| | |-- keywr_defaultBoardcfg_pm_hex.h
| | |-- keywr_defaultBoardcfg_rm_hex.h
| | `-- keywr_defaultBoardcfg_security_hex.h
| `-- j721e
| |-- keywr_defaultBoardcfg_hex.h
| |-- keywr_defaultBoardcfg_pm_hex.h
| |-- keywr_defaultBoardcfg_rm_hex.h
| `-- keywr_defaultBoardcfg_security_hex.h
|-- build
| |-- bin2c.mk
| `-- keywriter.mk
|-- init.asm
|-- keywriter_component.mk
|-- main.c
|-- main.h
|-- scripts
| |-- construct_ext_otp_data.sh
| |-- generate_test_binaries.sh
| |-- gen_keywr_cert_helpers.sh
| |-- gen_keywr_cert.sh
| |-- templates
| | |-- config_bmpk_template.txt
| | `-- config_template.txt
|-- soc
| |-- common
| | |-- linker.lds
| | `-- pmic_example.c
| |-- j7200
| | |-- keywriter_utils.c
| | `-- keywriter_utils.h
| `-- j721e
| |-- keywriter_utils.c
| `-- keywriter_utils.h
|-- tifs_bin
| |-- j7200
| `-- j721e
`-- x509cert
4.14.4. Important Features & Details¶
- VPP must be powered (1.8v) when the efuses are programmed. Refer to device datasheet for details on VPP requirements.
Note
Refer soc/$(SOC)/keywriter_utils.c for an example usage of I2C request
to enable VPP power from PMIC under I2C control.
Alternately, direct control of an LDO via GPIO can be used.
- OTP keywriter firmware supports a maximum certificate length of 5400 bytes.
Important
This length is for individual certificates, and not the x509cert/final_certificate.bin.
Check size of primary_cert.bin and seconday_cert.bin (optional depending on
BMPK). If certificate length exceeds the supported limit, the keys can be programmed
using incremental approach.
- Incremental programming - Until the KEYREV value is set to either 1 or 2, the device is considered as HS-FS and key values can continue to be programmed incrementally. This allows key programming to be done in multiple passes. Refer this for detailed examples.
Example
Different offsets of extended OTP array could be programmed, followed by other keys such as MSV, SWREV etc.
Important
Once the KEYREV is set to 1 or 2, the device becomes HS-SE, and OTP keywriter application will no longer boot as the user root key takes over as root of trust. So programming KEYREV should be done in the last step.
- OTP keywriter supports J7200 & J721e SoCs
4.14.5. Build Procedure¶
- Download the OTP Keywriter add-on package, and copy the folders
docsandpackagesto PDK code base. - Generate x509 certificate containing key/efuse values from customer HSM
- Build PDK Keywriter app
- With the addition of J7200. Default is still J721e. For Building J7200 please specify SOC=j7200 BOARD=j7200_evm.
- Run on SoC, using a boot mode of choice
Note
OTP keywriter add-on package has the necessary firmware and TI FEK public key required to build the OTP keywriter example application.
4.14.5.1. Generating x509 certificate from customer HSM¶
The Customer keys are supposed to be private, and not to be distributed out in open. For the scope of this document, Customer HSM would mean The secure server/ system where the customer intends to generate the x509 certificate. Once the certificate is generated, since the customer key information is encrypted, it is safe to share the certificate in open without revealing the actual keys.
The customer provided key material consists of both Public Key hashes (xMPKH) and secret/secure symmetric keys (xMEK). In order to maintain security, the symmetric keys are encrypted on the secure server (referred to here as Customer HSM), so that the resulting X509 certificate can be exported and embedded in the Keywriter binary without exposing the secret keys.
Note
OpenSSL (1.1.1 11 Sep 2018) is required for building the OTP Keywriter. Check if OpenSSL is installed by typing “openssl version” at the comamnd prompt. If OpenSSL is not installed, download and install OpenSSL for your OS.
- For Windows : The easiest way is to download and install Strawberry Perl The Strawberry Perl installer automatically installs and sets up OpenSSL. Alternately, users can also use any of these Third Party OpenSSL Distributions for Windows. Refer individual links for instructions on how to setup OpensSSL using a particular distribution.
- For Linux : Execute the command
sudo apt-get install opensslat the linux command prompt.
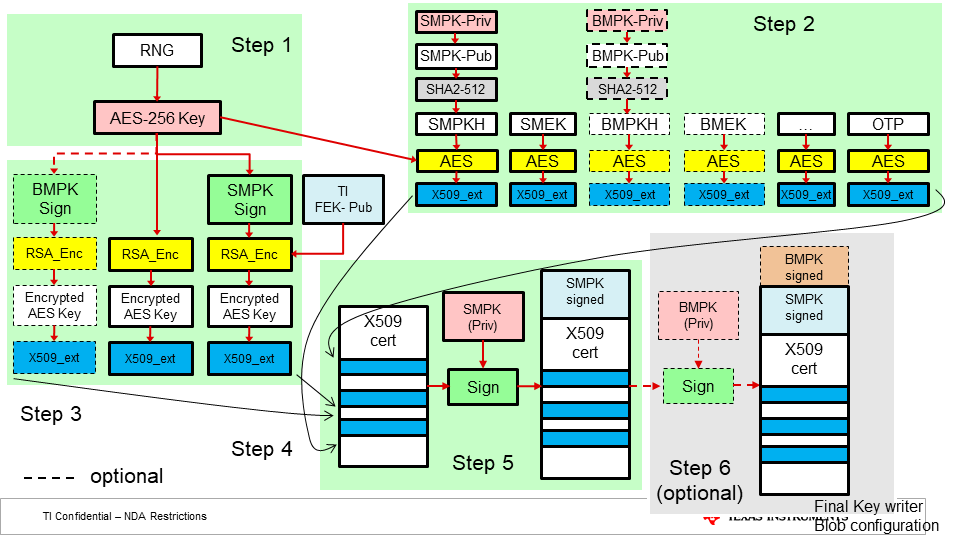
Fig. 4.8 X509 Certificate generation procedure.
- OEM generates a random 256-bit number to be used as an AES encryption key for protecting the OTP data.
- The AES-256 key from step 1 is used to encrypt all X509 extension fields, which require encryption protection.
- Following X509 extensions are created, using TI FEK (public):
- Encrypting the AES-256 key with TI FEK
- Signing the AES-256 key with the SMPK, and encrypting that with the TI FEK
- (optionally, refer step 6) signing the AES-256 key with the BMPK, and encrypting that with the TI FEK
- All of the extensions from steps 1-3 are combined into a X.509 configuration which is used to generate and sign a certificate with the SMPK.
- This X509 config is sigend using SMPK (priv).
- (Optional) If the OEM chooses to write BMPK/BMEK fields, X509 config from step 5 needs to be signed using BMPK (priv).
The scripts folder has the necessary tools for generating x509 certificate for eFuse programming. It can be copied to a secure server (customer HSM) where the customer keys are stored, and used to generate the x509 certificate.
Run the gen_keywr_cert.sh shell script, to create the certificate.
Modify the path arguments to specific keys as necessary. Use -h option for help.
./gen_keywr_cert.sh -h
Tip
./gen_keywr_cert.sh -gwill generate dummy keys for testing, inkeys/foldergen_keywr_cert.shwill also generate SHA-512 hash of SMPK, SMEK, BMPK, and BMEK and store them inverify_hash.csv. M3 UART logs will also print out SHA-512 hash of the keys.verify_hash.csvcan be used for quick comparision with M3 logs
The final certificate will be available in x509cert/final_certificate.bin in
customer HSM, which needs to be exported to PDK Keywriter app directory
x509cert/final_certificate.bin.
4.14.5.2. Extended OTP¶
Note
This extension is currently not supported, and reserved for future.
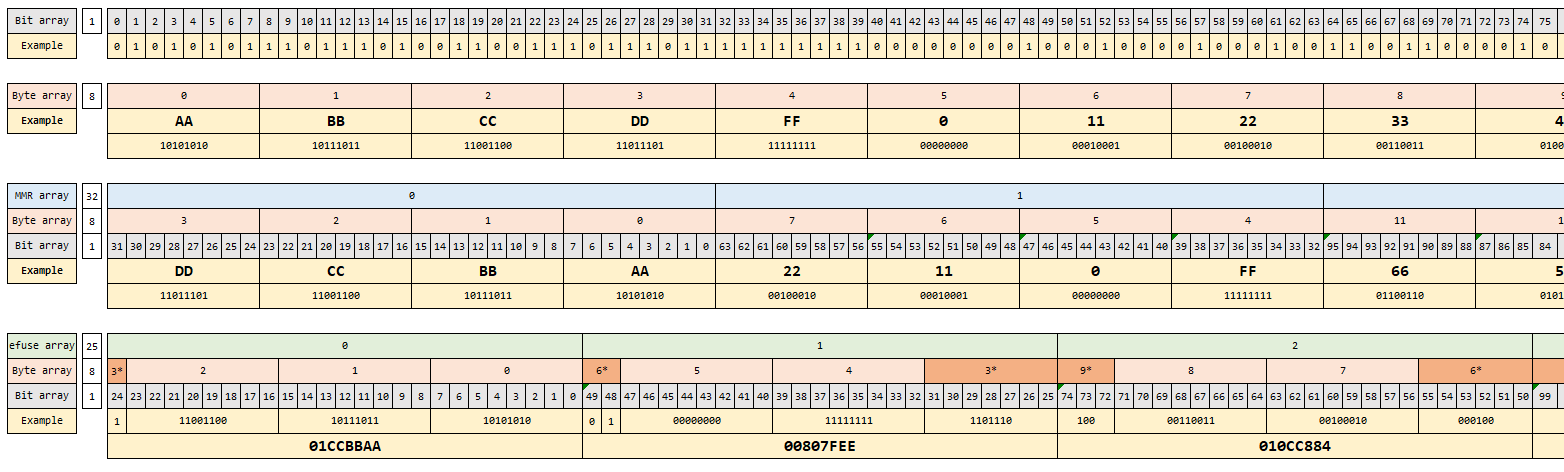
1024 bits are provided as input, out of which size number of bits starting from
index are programmed into efuses. Following figure illustrates the bit mapping
from byte array (input) to efuse array (efuse rows).
Example
If only byte array indexes 2 and 3 were to be programmed (0xCC, 0xDD respectively) from the above figure, we can see that efuse rows 0 and 1 would be programmed as (0x01CC0000) and (0x0000006E) with masks (0x01FF0000) and (0x0000007F) respectively.
If they were to be write protected, we have to write protect both row 0 and row 1.
So, we need to set wprp to 0000000000000003 0000000000000000
The MSB 16 octets are for wp, LSB 16 octets are for rp.
bits 0 and 1 are set in wp, to write protect efuse row 0 and row 1.
Please note that this would cause the remaining bits of row 0 and row 1 also to be write protected.
4.14.5.3. Building PDK Keywriter app¶
The keywriter app can be built with the following commands. In all below commands “make” can be replaced with “gmake” for Windows machine build. For more details about building the PDK, refer here.
Following files are needed before building keywriter example application
x509cert/final_certificate.bintifs_bin/j721e/ti-fs-keywriter.binx509cert/final_certificate.bin
cd <pdk-install-path>/packages/ti/build/
make keywriter_img_clean
make keywriter_img -j4
Final keywriter_img_<SoC>_release.tiimage is available at
<pdk-install-path>/packages/ti/boot/keywriter/binary/$(SOC)
Note
The OTP Keywriter certificate from x509cert/final_certificate.bin is appended to the pdk binary
<pdk-install-path>/packages/ti/boot/keywriter/binary/keywriter_img_j721e_release.bin
and signed. So that the source code does not need to be compiled each time there is a change
in the OTP Keywriter certificate.
Note
Building sciclient_boardcfg and sciclient_direct modules
before keywriter_img is no longer necessary, as the compiled .h files
for board config are included in <pdk-packages>/ti/boot/keywriter/boardcfgs/j721e
4.14.5.4. Running on SoC, using a boot mode of choice¶
The final keywriter_img_$(SOC)_release.tiimage is a standalone (without need for any SBL)
bootable keywriter applcation image containing the encrypted OTP keywrtiter firmware binary,
and OTP configuration (x509 certificate).
The PDK Keywriter app will load OTP Keywriter binary, and call OTP keywriter API using Sciclient service
The response from TISCI_MSG_KEY_WRITER, gives information about success/failure in customer key
programming in SoC eFuses.
This is logged on R5 UART Port, for confirmation to the user.
4.14.6. Debugging¶
The debug_response from
TISCI_MSG_KEY_WRITER
has detailed information about success / failure in blowing eFuses.
The enumeration documented here
has the bit positions, which are set in debug_response according to specific issue while programming customer keys.
A debug_response of 0x00 means programming was successful.
Apart from debug_response, there are MCU R5 and M3 UART logs which help in debugging.
Example logs, after a successful OTP Keywriter operation can be found here
4.14.7. Appendix¶
4.14.7.1. Using TI dummy keys from PDK code base¶
cd <PDK-INSTALL-PATH>
# Copy the customer dummy private key (SMPK private key, PEM format)
cp build/makerules/k3_dev_mpk.pem boot/keywriter/scripts/keys/smpk.pem
# Copy the customer dummy encryption key (SMEK, converted to binary file)
xxd -p -r build/makerules/k3_dev_mek.txt > boot/keywriter/scripts/keys/smek.key
4.14.7.2. Creating x509 certificates for Incremental Programming¶
4.14.7.2.1. Pass 1¶
OTP keywriter can program extended otp array, when supplied with an index, and size of bits to program (both index and size have to be muliples of 8).
Constructing extended otp array
# Step 1: Generate 1024 bit array ext_otp_data.bin
./construct_ext_otp_data.sh -extotp 0xFF -indx 0 -size 8
# Step 2: Edit ext_otp_data.txt for any more changes
vim ext_otp_data.txt
# Step 3: Convert txt to bin file
xxd -r -p ext_otp_data.txt > ext_otp_data.bin
# Setp 4: Generate x509 certificate
./gen_keywr_cert.sh -t ti_fek_public.pem --ext-otp ext_otp_data.bin --ext-otp-indx 0 --ext-otp-size 8
Note
Steps 2, 3 can be skipped if no changes are needed in extended OTP array
After creating this certificate, building the example keywriter app, and programming ext_otp[0:7], we could also program another offset of ext_otp
4.14.7.2.2. Pass 2¶
./construct_ext_otp_data.sh -extotp 0x1234 -indx 8 -size 16
./gen_keywr_cert.sh -t ti_fek_public.pem --ext-otp ext_otp_data.bin --ext-otp-indx 8 --ext-otp-size 16 --ext-otp-wprp 00000000000000010000000000000000
Note
The index and size arguments should be same in both the commands
This will create another certificate. Keywriter example app needs to be built after every change in certificate. This could be reapeated many times, but without any overlap in the ext_otp index, size parameters.
4.14.7.2.3. Pass 3¶
Since the KEYREV value is not modified until now, we can still use OTP keywriter to program other keys.
Following code snippet would set SMPKH, SMEK, MSV, KEYCNT and KEYREV.
Note
It is recommended to write protect SMPKH, SMEK, BMPKH, BMEK efuse rows by
providing the specific arguments to gen_keywr_cert.sh script.
./gen_keywr_cert.sh -s keys/smpk.pem -s-wp
--smek keys/smek.key --smek-wp -t ti_fek_public.pem
-a keys/aes256.key --msv 0xC0FFE --msv-wp --keycnt 1 --keyrev 1
Important
- KEYCNT should match the number of keys programmed into efuses.
- KEYREV should always be
<=KEYCNT - It is recommended to write protect KEYCNT
- KEYREV could be left without write protection, if a run time KEYREV update is needed.
4.14.7.3. X509 Configuration Template¶
The following x509 configuration template is used, by gen_keywr_cert.sh file,
to create the x509 certificate. Each key has an extension field
(OID 1.3.6.1.4.1.294.1.64 - 1.3.6.1.4.1.294.1.81), mentioning information such as SHA-512
value, size, IV, RS used in AES encryption.
Details about individual extensions can be obtained form Security x509 Certificate Documentation
[ req ]
distinguished_name = req_distinguished_name
x509_extensions = v3_ca
prompt = no
dirstring_type = nobmp
# This information will be filled by the end user.
# The current data is only a place holder.
# System firmware does not make decisions based
# on the contents of this distinguished name block.
[ req_distinguished_name ]
C = oR
ST = rx
L = gQE843yQV0sag
O = dqhGYAQ2Y4gFfCq0t1yABCYxex9eAxt71f
OU = a87RB35W
CN = x0FSqGTPWbGpuiV
emailAddress = kFp5uGcgWXxcfxi@vsHs9C9qQWGrBs.com
[ v3_ca ]
basicConstraints = CA:true
1.3.6.1.4.1.294.1.64 = ASN1:SEQUENCE:enc_aes_key
1.3.6.1.4.1.294.1.65 = ASN1:SEQUENCE:enc_smpk_signed_aes_key
1.3.6.1.4.1.294.1.66 = ASN1:SEQUENCE:enc_bmpk_signed_aes_key
1.3.6.1.4.1.294.1.67 = ASN1:SEQUENCE:aesenc_smpkh
1.3.6.1.4.1.294.1.68 = ASN1:SEQUENCE:aesenc_smek
1.3.6.1.4.1.294.1.69 = ASN1:SEQUENCE:plain_mpk_options
1.3.6.1.4.1.294.1.70 = ASN1:SEQUENCE:aesenc_bmpkh
1.3.6.1.4.1.294.1.71 = ASN1:SEQUENCE:aesenc_bmek
1.3.6.1.4.1.294.1.72 = ASN1:SEQUENCE:plain_mek_options
1.3.6.1.4.1.294.1.73 = ASN1:SEQUENCE:aesenc_user_otp
1.3.6.1.4.1.294.1.74 = ASN1:SEQUENCE:plain_key_rev
1.3.6.1.4.1.294.1.76 = ASN1:SEQUENCE:plain_msv
1.3.6.1.4.1.294.1.77 = ASN1:SEQUENCE:plain_key_cnt
1.3.6.1.4.1.294.1.78 = ASN1:SEQUENCE:plain_swrev_sysfw
1.3.6.1.4.1.294.1.79 = ASN1:SEQUENCE:plain_swrev_sbl
1.3.6.1.4.1.294.1.80 = ASN1:SEQUENCE:plain_swrev_sec_brdcfg
1.3.6.1.4.1.294.1.81 = ASN1:SEQUENCE:plain_keywr_min_version
[ enc_aes_key ]
# Replace PUT-ENC-AES-KEY with acutal Encrypted AES Key
val = FORMAT:HEX,OCT:PUT_ENC_AES_KEY
size = INTEGER:PUT_SIZE_ENC_AES
[ enc_bmpk_signed_aes_key ]
# Replace PUT-ENC-BMPK-SIGNED-AES-KEY with acutal Encrypted BMPK signed AES Key
val = FORMAT:HEX,OCT:PUT_ENC_BMPK_SIGNED_AES_KEY
size = INTEGER:PUT_SIZE_ENC_BMPK_SIGNED_AES
[ enc_smpk_signed_aes_key ]
# Replace PUT-ENC-SMPK-SIGNED-AES-KEY with acutal Encrypted SMPK signed AES Key
val = FORMAT:HEX,OCT:PUT_ENC_SMPK_SIGNED_AES_KEY
size = INTEGER:PUT_SIZE_ENC_SMPK_SIGNED_AES
[ aesenc_smpkh ]
# Replace PUT-AESENC-SPMKH with acutal Encrypted AES Key
val = FORMAT:HEX,OCT:PUT_AESENC_SMPKH
iv = FORMAT:HEX,OCT:PUT_IV_AESENC_SMPKH
rs = FORMAT:HEX,OCT:PUT_RS_AESENC_SMPKH
size = INTEGER:PUT_SIZE_AESENC_SMPKH
action_flags = INTEGER:PUT_ACTFLAG_AESENC_SMPKH
[ aesenc_smek ]
# Replace PUT-AESENC-SMEK with acutal Encrypted AES Key
val = FORMAT:HEX,OCT:PUT_AESENC_SMEK
iv = FORMAT:HEX,OCT:PUT_IV_AESENC_SMEK
rs = FORMAT:HEX,OCT:PUT_RS_AESENC_SMEK
size = INTEGER:PUT_SIZE_AESENC_SMEK
action_flags = INTEGER:PUT_ACTFLAG_AESENC_SMEK
[ aesenc_bmpkh ]
# Replace PUT-AESENC-BMPKH with acutal Encrypted BMPKH
val = FORMAT:HEX,OCT:PUT_AESENC_BMPKH
iv = FORMAT:HEX,OCT:PUT_IV_AESENC_BMPKH
rs = FORMAT:HEX,OCT:PUT_RS_AESENC_BMPKH
size = INTEGER:PUT_SIZE_AESENC_BMPKH
action_flags = INTEGER:PUT_ACTFLAG_AESENC_BMPKH
[ aesenc_bmek ]
# Replace PUT-AESENC-BMEK with acutal Encrypted BMEK
val = FORMAT:HEX,OCT:PUT_AESENC_BMEK
iv = FORMAT:HEX,OCT:PUT_IV_AESENC_BMEK
rs = FORMAT:HEX,OCT:PUT_RS_AESENC_BMEK
size = INTEGER:PUT_SIZE_AESENC_BMEK
action_flags = INTEGER:PUT_ACTFLAG_AESENC_BMEK
[ plain_msv ]
# Replace PUT-PLAIN-MSV with actual MSV value
val = FORMAT:HEX,OCT:PUT_PLAIN_MSV
action_flags = INTEGER:PUT_ACTFLAG_PLAIN_MSV
[ plain_mpk_options ]
# Replace PUT-PLAIN-MPK-OPT with actual MPK OPT value
val = FORMAT:HEX,OCT:PUT_PLAIN_MPK_OPT
action_flags = INTEGER:PUT_ACTFLAG_PLAIN_MPK_OPT
[ plain_mek_options ]
# Replace PUT-PLAIN-MEK-OPT with actual MEK OPT value
val = FORMAT:HEX,OCT:PUT_PLAIN_MEK_OPT
action_flags = INTEGER:PUT_ACTFLAG_PLAIN_MEK_OPT
[ plain_key_rev ]
# Replace PUT-PLAIN-KEY-REV with actual Key Rev value
val = FORMAT:HEX,OCT:PUT_PLAIN_KEY_REV
action_flags = INTEGER:PUT_ACTFLAG_PLAIN_KEY_REV
[ plain_key_cnt ]
# Replace PUT-PLAIN-KEY-CNT with actual Key Count value
val = FORMAT:HEX,OCT:PUT_PLAIN_KEY_CNT
action_flags = INTEGER:PUT_ACTFLAG_PLAIN_KEY_CNT
[ plain_swrev_sysfw ]
# Replace PUT-PLAIN-SWREV-SYSFW with actual SWREV SYSFW value
val = FORMAT:HEX,OCT:PUT_PLAIN_SWREV_SYSFW
action_flags = INTEGER:PUT_ACTFLAG_PLAIN_SWREV_SYSFW
[ plain_swrev_sbl ]
# Replace PUT-PLAIN-SWREV-SBL with actual SWREV SBL value
val = FORMAT:HEX,OCT:PUT_PLAIN_SWREV_SBL
action_flags = INTEGER:PUT_ACTFLAG_PLAIN_SWREV_SBL
[ plain_swrev_sec_brdcfg ]
# Replace PUT-PLAIN-SWREV-SEC-BRDCFG with actual SWREV SEC BRDCFG value
val = FORMAT:HEX,OCT:PUT_PLAIN_SWREV_SEC_BRDCFG
action_flags = INTEGER:PUT_ACTFLAG_PLAIN_SWREV_SEC_BRDCFG
[plain_keywr_min_version ]
# Replace PUT-PLAIN-KEYWR-MIN-VER with actual KEYWR-MIN-VER value
val = FORMAT:HEX,OCT:PUT_PLAIN_KEYWR_MIN_VER
[ aesenc_user_otp ]
# Replace PUT-AESENC-USER-OTP with actual Encrypted OTP
val = FORMAT:HEX,OCT:PUT_AESENC_USER_OTP
iv = FORMAT:HEX,OCT:PUT_IV_AESENC_USER_OTP
rs = FORMAT:HEX,OCT:PUT_RS_AESENC_USER_OTP
wprp = FORMAT:HEX,OCT:PUT_WPRP_AESENC_USER_OTP
index = INTEGER:PUT_INDX_AESENC_USER_OTP
size = INTEGER:PUT_SIZE_AESENC_USER_OTP
action_flags = INTEGER:PUT_ACTFLAG_AESENC_USER_OTP
4.14.7.4. OTP KEYWRITER LOGS¶
R5 Log
OTP Keywriter Version: 02.00.00.00 (Jun 15 2021 - 10:59:55)
OTP Keywriter ver: 21.5.0-v2021.05-9-gde058 (Terri
OTP_VppEn
test_pmic_i2c_lld_intf_setup(): 496: PMIC_MAIN_INST I2C Setup...
test_pmic_i2c_lld_intf_setup(): 536: done...
I2C1: Passed for address 0x4c !!!
I2C1: Passed for address 0x13 !!!
INT STAT[0]: 0x00000000
INT STAT[1]: 0x00000000
INT STAT[2]: 0x00000000
INT STAT[3]: 0x00000000
volate_mV: 1800
Key programming sequence initialted
Taking OTP certificate from 0x41c73004
Debug response: 0x0
Key programming sequence completed
M3 Log
#
# Decrypting extensions..
#
MPK Options: 0x21
MEK Options: 0x1
MPK Opt P1: 0x1
MPK Opt P2: 0x1
MEK Opt : 0x1
SMPKH extension disabled
SMEK extension disabled
* BMPKH Part 1 BCH code: 8180dd66
* BMPKH Part 2 BCH code: 81873fe5
* BMPK Hash (part-1,2):
384be278a7a50eb25afdffac2e8bd306f82a3b51a770f8056c9ddeb9f31b0d3d01
3ea0063e6de3127a47c8a1443fc7e10dadffb51601aeaeb499d607e02874cd8001
* BMEK BCH code: c1bbe2be
* BMEK Hash: 9352f2c8069698ad4a1e6dfb381723ba4a15948a5e00c5ac004f574f194efe66bc701d378b01ec0bf1a36bef6e7a931d466dbdb38bd2be0aad8afc756aa5ea7a
EXT OTP extension disabled
MSV extension disabled
KEY CNT extension disabled
KEY REV extension disabled
SWREV extension disabled
FW CFG REV extension disabled
* KEYWR VERSION: 0x20000
#
# Programming Keys..
#
* MSV:
[u32] bch + msv: 0x8BAC0FFE
MSV extension disabled
[u32] bch + msv: 0x8BAC0FFE
* SWREV:
SWREV extension disabled
* FW CFG REV:
SWREV SEC BCFG extension disabled
* EXT OTP:
EXT OTP extension disabled
* BMPKH, BMEK:
Programmed 11/11 rows successfully
Programmed 2/2 rows successfully
Programmed 11/11 rows successfully
Programmed 2/2 rows successfully
Programmed 11/11 rows successfully
Programmed 2/2 rows successfully
* SMPKH, SMEK:
SMPKH extension disabled
SMEK extension disabled
* KEYCNT:
[u32] keycnt: 0x0
KEY CNT extension disabled
[u32] keycnt: 0x0
* KEYREV:
[u32] keyrev: 0x0
KEY REV extension disabled
[u32] keyrev: 0x0
4.14.7.6. OTP Keywriter validation¶
Following is the validation procedure used on OTP keywriter, these
steps can be replicated by using the script
<keywriter_dir>/scripts/generate_test_binaries.sh
| Pass | Details | Value | Purpose |
|---|---|---|---|
| 1 | Program MSV | 0xC0FFE | Demonstrates that MSV can be programmed successfully |
| 2 | SWREV (SBL+SYSFW) | sbl: 3, sysfw: 4 | Skip this step - DO NOT PROGRAM |
| 3 | SWREV (SEC BCFG) | sec-bcfg: 5 | Skip this step - DO NOT PROGRAM |
| 4 | EXT OTP (31:0) bits (32 bits) | 0x80000001 | Ensures that you can program ext_otp area, of size more than 25 bits correctly |
| 5 | EXT OTP (39:32) bits (8 bits) | 0x81 | Ensures that incremental programming is possible for ext otp |
| 6 | (WP) Program BMPKH, BMEK (set as dummy key bmpk val) | Dummy keys are programmed | |
| 7 | (WP) Program SMPKH, SMEK (set as dummy key smpk val) | Dummy keys are programmed | |
| 8 | (WP) Program KEYCNT 2 | 2 (0x0303) | Key count progammed |
| 9 | (~WP) Program KEYREV 1 | 1 (0x0101) | After reboot, device will be HS-SE, use smpk for signing the SBL and boardconfigs |