Some bootflow changes have been introduced in MCU+SDK, this document aims to explain the changes and is majorly meant for users of older SDK wanting to upgrade to the new flow.
| Normal Bootflow(OLD) | Combined Bootflow(NEW) |
|---|---|
| 1. Power On Reset | 1. Power On Reset |
| 2. ROM Bootloader (RBL) loads Secondary Bootloader (SBL) | 2. ROM Bootloader (RBL) loads SBL, SYSFW, and boardcfg together as one binary blob |
| 3. SBL loads SYSFW, and sets boardcfg | 3. SBL waits for SYSFW to boot up |
| 4. SBL loads application image(s) | 4. SBL loads application image(s) |
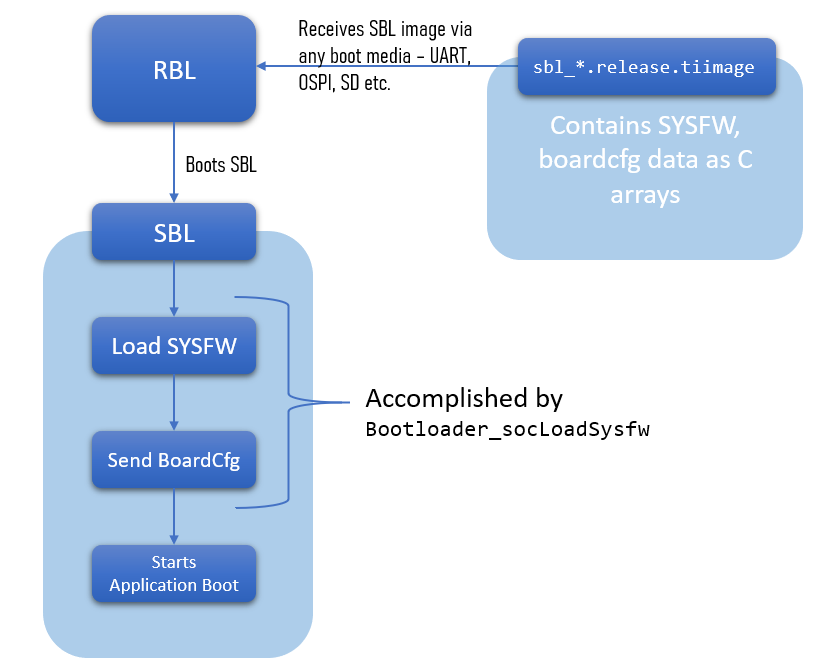
Sciclient_loadFirmware used for this purpose. We created a wrapper API which calls this API, Bootloader_socLoadSysfw. It can be seen that this API is pretty much the first one to be invoked in the main() of the SBL. This API will also set the boardcfg, by calling the appropriate Sciclient APIs..rodata section when building the SBL application. This is wasted memory and will add to the size of SBL final image.can be used by applications. Also since the SYSFW and boardcfg data is not part of the build flow, the same libraries and SBLs can be used for secure/non-secure devices. Given below is a similar flow diagram for combined boot flow.
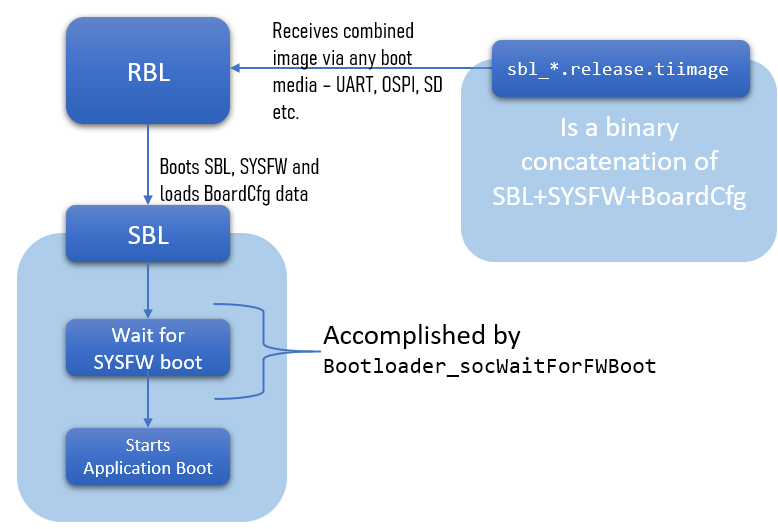
Bootloader_socLoadSysFw API missing : Since SBL no longer needs to load SYSFW, the Bootloader_socLoadSysFw() was removed to decrease the library size.x509Certificate.sh/x509Certificate.ps1 scripts under tools/boot/signing in the SDK. This script generates an x509 certificate for the SBL binary and append it to the SBL binary to create the final *.tiimage file. This signing and certificate appendment is required for ROM boot.In combined boot flow, we use a new script, rom_image_gen.py to generate the final *.tiimage which will be booted by the ROM.
If you are someone who doesn't use the SDK build system, you can take a look at the makefiles of any SBL examples to understand the usage of rom_image_gen.py script and take this into your build system as well.
Usage print of rom_image_gen.py is as follows:
As you can see, the SBL binary and SYSFW binary among other things are combined together to form the final image as opposed to x509Certificate.sh/ps1 script generating x509 certificate for SBL alone.